SSL Certificate
Deploy an SSL certificate to enable HTTPS encryption of websites, trusted identity authentication and prevent against data leaks or tampering during transmission.
Get SSL Certificate >Blog > Thoughts on Google Chrome Distrusts Entrust—Are Trusted CA Still Trustworthy?
Tag:
Entrust
CA
Distrust
Certificate Lifecycle Management
864:0
Eric Z.August 16 2024
On June 27th, Google Chrome has announced that multiple Entrust root certificates will no longer be trustworthy after October 31st, 2024. This incident has a relatively large impact on the industry, and has caused widespread concern and deep reflection in the field of cyber security.
Entrust, once known as one of the oldest CAs, now has to face the fate of being discarded by the mainstream browser. What happened to Entrust discloses that trusted certificates might be distrusted anytime or be trusted only for the moment. The credibility of trusted CAs have been deeply questioned cross-industry. It is like a domino effect even reaching further. The so-called trusted CA certificates are merely built upon the approval of browser companies. It is so fragile that without browsers’ recognition, CA certificates could be disrupted at any time.
Browser manufacturers act increasingly like industry “dictators,” making arbitrary decisions by a virtue of their market status. It is like “Power Games.” Not only makes CA institutions feel lowly in their position, but also casts a shadow on the fairness of the entire industry, not sure who will be "dis-trusted" next.
Since Entrust has been canceled, the author found that many peers began to compete for Entrust customers, and to provide Entrust customer transfer solutions on their websites. It looks like Entrust is an appetizer on the menu. In fact, all the other CAs are listed on the menu, and Google, Microsoft, Firefox and other browser or operating system companies are the ones looking at the menu.
Imagine
↓↓↓
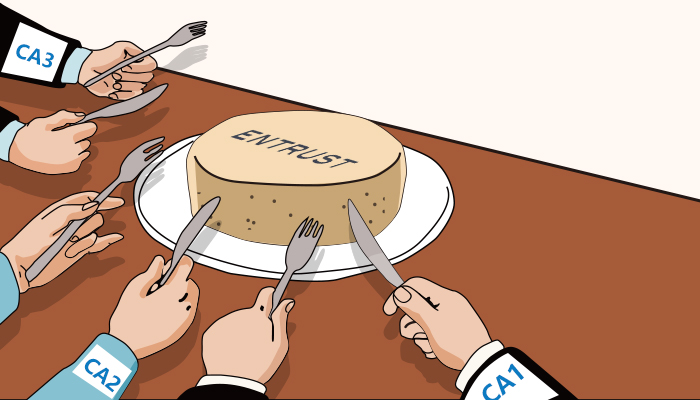
actual
↓↓↓

Based on different cases, under the rules dominated by browser companies, there exits no eternal trustworthiness but only temporary. As for end users, while searching for a current trusted CA, it is necessary to reflect on how to establish a stabler credible system. Relying on only one trusted CA institution is far from enough. More importantly is to have the choices of multiple CAs, constructing a flexible and effective SSL certificates management system at the same time. In the face of rapid and potential changes, make sure the continuity of the service.
After consecutive CA untrusted events occur, it is crucial to apply SSL/TLS Certificate Lifecycle Management configured with multiple CAs for enterprises.
Multiple CAs SSL Certificate Lifecycle management would easily help corporations to switch to another trusted CA if encounter distrusted CA.
In addition to one-click certificate brand replacement, it is also important to solve the problem of large-scale deployment of SSL certificates. CLM is able to complete tasks like automatically applying for SSL certificates, download, renew, reissue, revoke SSL certificates and change brands, etc. Moreover, CLM carries out various functions: auto discovery of SSL certificates, auto renew, auto deployment, real-time monitoring, log management, providing multiple public CAs portals, pre-warning and compliance judgment, etc.
Nine Basic Functions of SSL Certificate Lifecycle Management
SSL Certificate Lifecycle Management 9 basic functions minimize the complexity of certificate management, and response to changes in the industry flexibly. Truly achieve automated operation and maintenance!
Above described 9 basic functions of SSL Certificate Lifecycle Management, sslTrus CLM SaaS includes them all. Not only that, sslTrus CLM is for FREE.

Enterprises buy SSL certificates at NicSRS, CLM package is completely free. This preferential policy undoubtedly reduces the operating costs of enterprises, but also improves the convenience and security of certificate management.
As a comprehensive and effective digital certificates management service tool, precisely tracking certificates, compliance monitoring in full-scale , and with a timely pre-warning system, sslTrus CLM helps enterprises easily cope with the challenges of digital certificate management and ensures that corporate information security is impeccable.
In the future development, we will keep enhancing our technological R&D and innovating creatively to provide more thorough digital certificates management solution. Jointly make the progress and contribute to the development of the industry.
If you want to know more about sslTrus CLM and use for free, please contact us anytime.
RELATED
2025-02-25 14:33:23
2025-02-18 10:58:56
2025-02-14 14:41:07
2025-02-08 17:31:15
2025-02-05 18:04:51
Categories

Free SSL Tools
Top Posts
Comments